Active Directory
Support level: Community
Preparation
The following placeholders are used in this guide:
ad.companyis the name of the Active Directory domain.authentik.companyis the FQDN of the authentik install.
Active Directory configuration
To support the integration of Active Directory with authentik, you need to create a service account in Active Directory.
-
Open Active Directory Users and Computers on a domain controller or computer with Active Directory Remote Server Administration Tools installed.
-
Navigate to an Organizational Unit, right click on it, and select New > User.
-
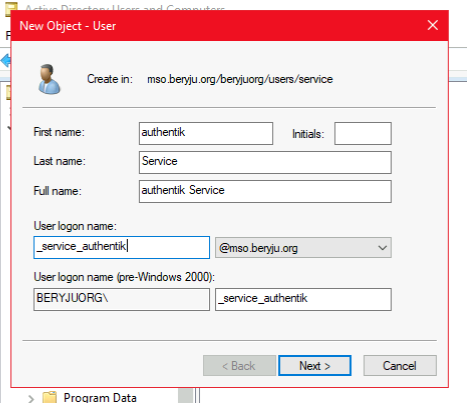
Create a service account, matching your naming scheme, for example:
-
Set the password for the service account. Ensure that the Reset user password and force password change at next logon option is not checked.
Either one of the following commands can be used to generate the password:
pwgen 64 1openssl rand 36 | base64 -w 0 -
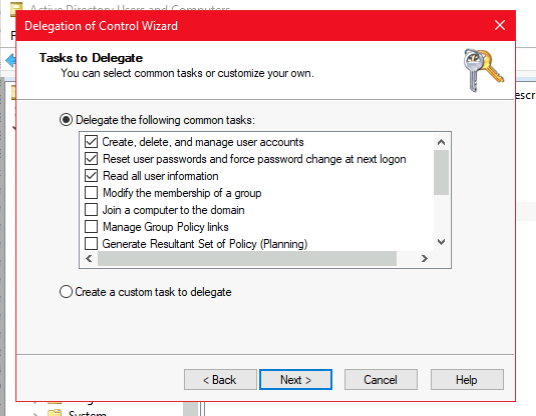
Open the Delegation of Control Wizard by right-clicking the domain Active Directory Users and Computers, and selecting All Tasks.
-
Select the authentik service account that you've just created.
-
Grant these additional permissions (only required when User password writeback is enabled on the LDAP source in authentik, and dependent on your AD Domain)
authentik Setup
To support the integration of authentik with Active Directory, you will need to create a new LDAP Source in authentik.
-
Log in to authentik as an admin, and open the authentik Admin interface.
-
Navigate to Directory > Federation & Social login.
-
Click Create and select LDAP Source as the type.
-
Provide a name, slug, and the following required configurations:
Under Connection Settings:
- Server URI:
ldap://ad.company
noteFor authentik to be able to write passwords back to Active Directory, make sure to use
ldaps://as a prefix. You can verify that LDAPS is working by opening theldp.exetool on a domain controller and attempting a connection to the server via port 636. If a connection can be established, LDAPS is functioning as expected. More information can be found in the Microsoft LDAPS documentation.Multiple servers can be specified by separating URIs with a comma (e.g.
ldap://dc1.ad.company,ldap://dc2.ad.company). If a DNS entry with multiple records is used, authentik will select a random entry when first connecting.- Bind CN:
<service account>@ad.company - Bind Password: the password of the service account created in the previous section.
- Base DN: the base DN which you want authentik to sync.
Under LDAP Attribute Mapping:
- User Property Mappings: select all Mappings which start with "authentik default LDAP" and "authentik default Active Directory"
- Group Property Mappings: select "authentik default LDAP Mapping: Name"
Under Additional Settings (optional) configurations that may need to be adjusted based on the setup of your domain:
- Group: if enabled, all synchronized groups will be given this group as a parent.
- Addition User/Group DN: additional DN which is prepended to your Base DN configured above, to limit the scope of synchronization for Users and Groups.
- User object filter: which objects should be considered users (e.g.
(objectClass=user)). For Active Directory set it to(&(objectClass=user)(!(objectClass=computer)))to exclude Computer accounts. - Group object filter: which objects should be considered groups (e.g
(objectClass=group)). - Lookup using a user attribute: acquire group membership from a User object attribute (
memberOf) instead of a Group attribute (member). This works with directories and nested groups memberships (Active Directory, RedHat IDM/FreeIPA), usingmemberOf:1.2.840.113556.1.4.1941:as the group membership field. - Group membership field: the user object attribute or the group object attribute that determines the group membership of a user (e.g.
member). If Lookup using a user attribute is set, this should be a user object attribute, otherwise a group object attribute. - Object uniqueness field: a user attribute that contains a unique identifier (e.g.
objectSid).
- Server URI:
-
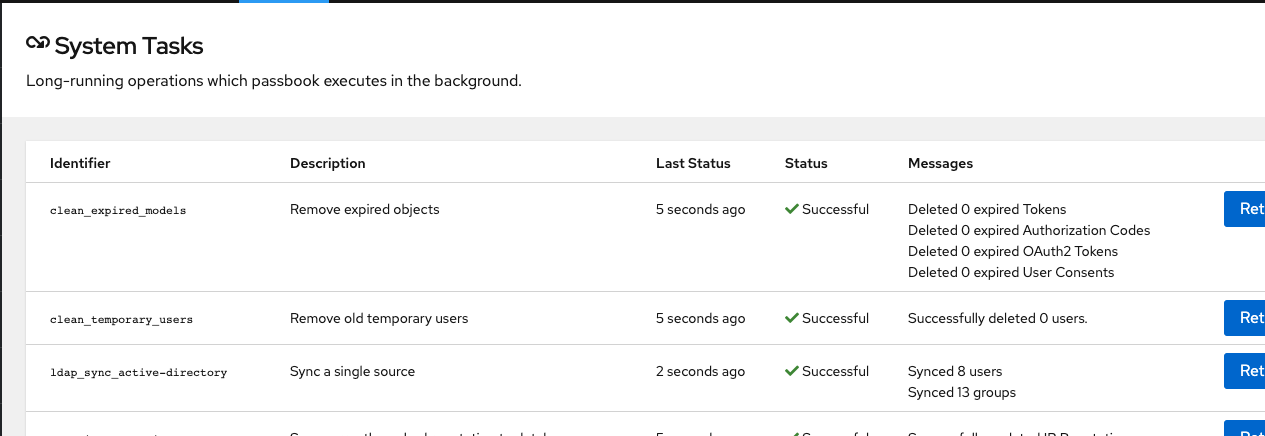
Click Finish to save the LDAP Source. An LDAP synchronization will begin in the background. Once completed, you can view the summary by navigating to Dashboards > System Tasks:
-
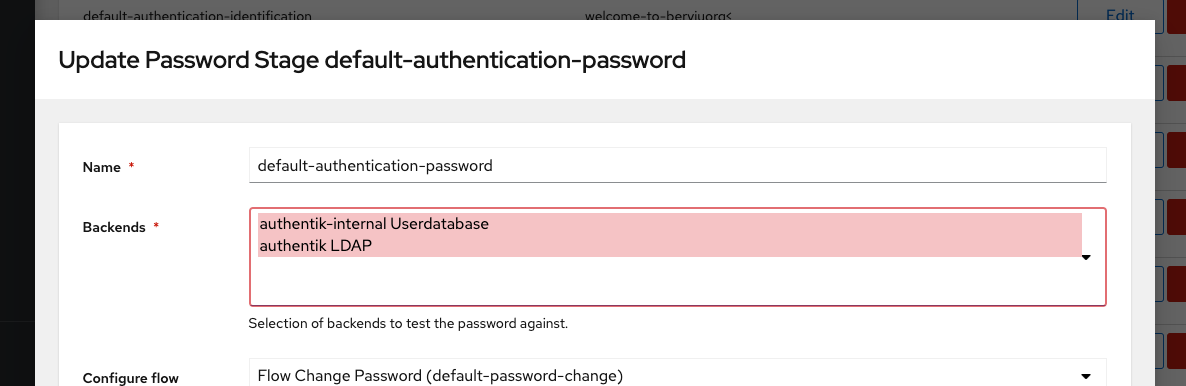
To finalise the Active Directory setup, you need to enable the backend "authentik LDAP" in the Password Stage.