Flows
Flows are a major component in authentik. In conjunction with stages and policies, flows are at the heart of our system of building blocks, used to define and execute the workflows of authentication, authorization, enrollment, and user settings.
There are over a dozen default, out-of-the-box flows available in authentik. Users can decide if they already have everything they need with the default flows or if they want to create their own custom flow, using the Admin interface, Terraform, or via the API.
A flow is a method of describing a sequence of stages. A stage represents a single verification or logic step. By connecting a series of stages within a flow (and optionally attaching policies as needed) you can build a highly flexible process for authenticating users, enrolling them, and more.
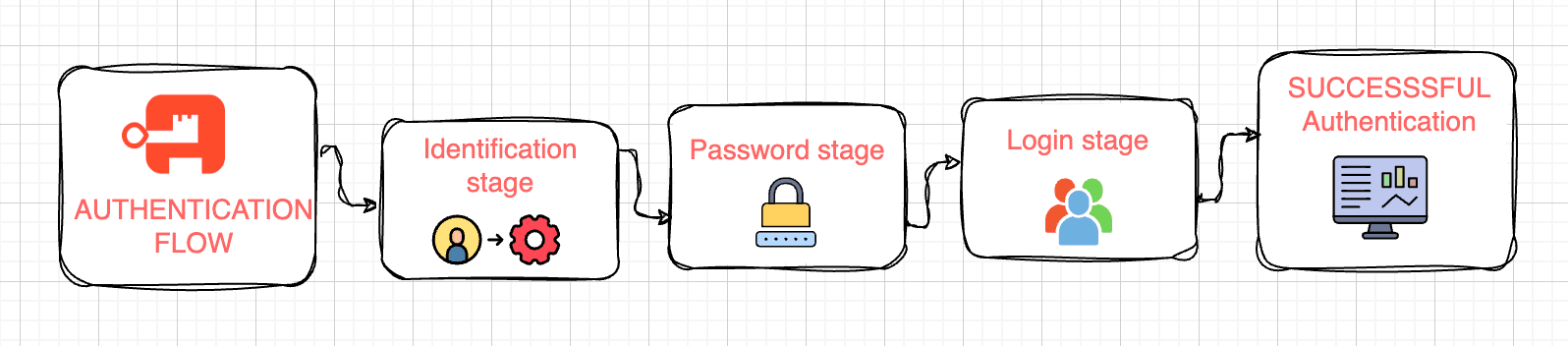
For example a standard login flow would consist of the following stages:
- Identification stage: user identifies themselves via a username or email address
- Password stage: the user's password is checked against the hash in the database
- Login stage: this stage attaches a currently pending user to the current session
When these stages are successfully completed, authentik logs in the user.
By default, policies are evaluated dynamically, right before the stage (to which a policy is bound) is presented to the user. This flexibility allows the login process to continue, change, or stop, based on the success or failure of each policy.
This default behaviour can be altered by enabling the Evaluate when flow is planned option on the stage binding. With this setting a flow plan containing all stages is generated upon flow execution. This means that all attached policies are evaluated upon execution. For more information about flow plans, read our flow context documentation.
Policies and permissions
Flows can have policies assigned to them. These policies determine if the current user is allowed to see and use this flow.
Keep in mind that in certain circumstances, policies cannot match against users and groups as there is no authenticated user yet.
Import or export a flow
Flows can be imported and exported (as blueprints) to share with other people, the community, and for troubleshooting.
Flows can be imported to add new functionality to existing flows, or to add a new custom flow.
You can download our Example flows and then import them into your authentik instance, or create a new flow.
Starting with authentik 2022.8, flows are exported as YAML, but legacy JSON-based flows can still be imported.
Flow imports are blueprint files, which may contain objects other than flows (such as policies, users, groups, etc).
You should only import files from trusted sources and review blueprints before importing them.
Create a custom flow
To create a flow, follow these steps:
- Log in to authentik as an administrator and open the Admin interface.
- In the Admin interface, navigate to Flows and Stages > Flows.
- Click Create, define the flow using the configuration settings described below, and then click Finish.
After creating the flow, you can then bind specific stages to the flow and bind policies to the flow to further customize the user's log in and authentication process.
To determine which flow should be used, authentik will first check which default authentication flow is configured in the active Brand. If no default is configured there, the policies in all flows with the matching designation are checked, and the first flow with matching policies sorted by slug will be used.
Flow configuration options
When creating or editing a flow in the UI of the Admin interface, you can set the following configuration options.
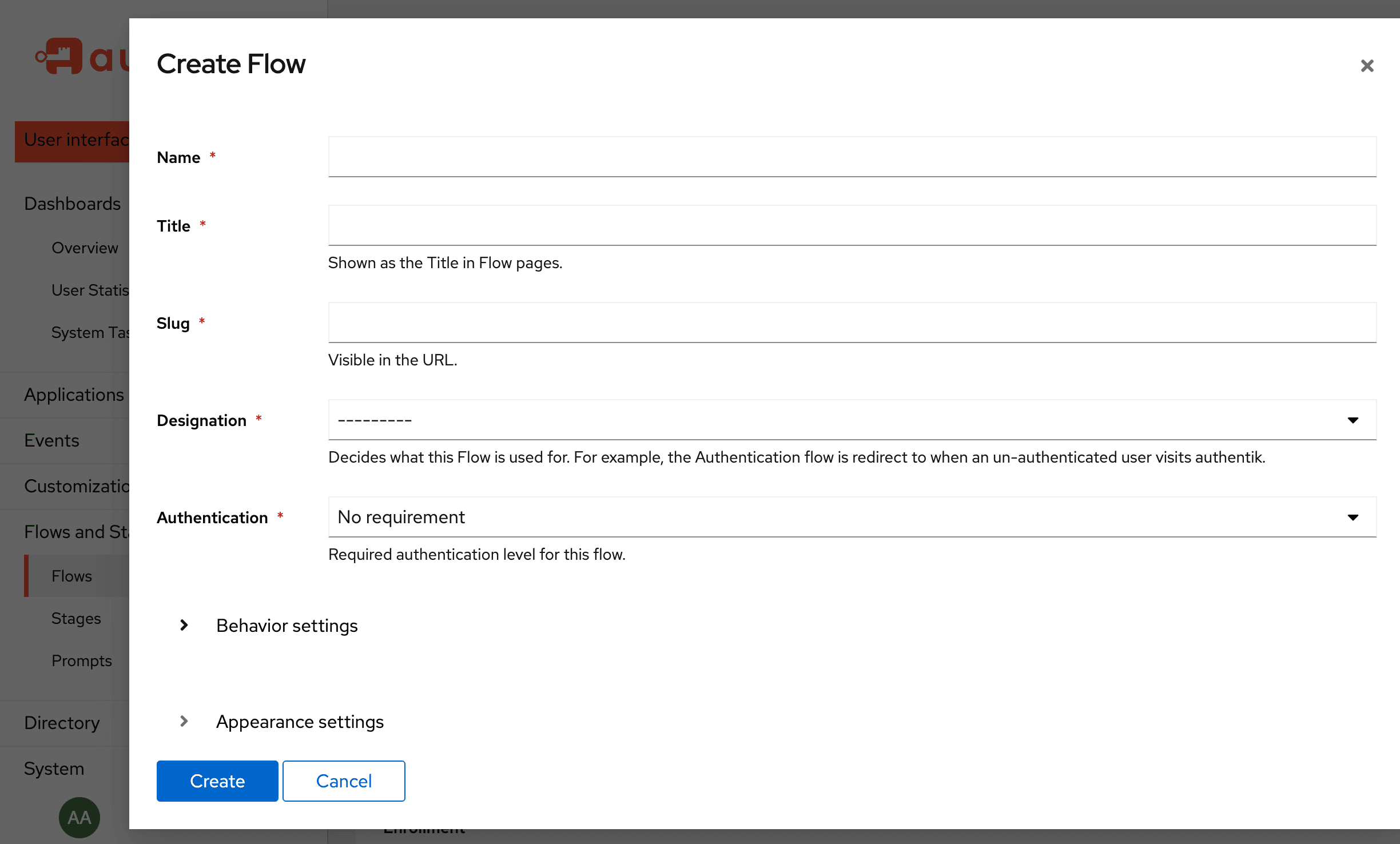
Name: Enter a descriptive name. This is the name that will appear on the list of flows in the Admin interface.
Title: This is the title that will appear on the flow as the end-user logs in and encounters the flow.
Slug: The slug will be used, and appear, in the URL when the flow is in use.
Designation: Flows are designated for a single purpose. This designation changes when a flow is used. The following designations are available:
-
Authentication: this option designates a flow to be used for authentication. The authentication flow should always contain a User Login stage, which attaches the staged user to the current session.
-
Authorization: designates a flow to be used for authorization of an application. Can be used to add additional verification steps before the user is allowed to access an application. This flow is defined per provider, when the provider is created, to state whether implicit or explicit authorization is required.
-
Enrollment: designates a flow for enrollment. This flow can contain any amount of verification stages, such as Email or Captcha. At the end, to create the user, you can use the User Write stage, which either updates the currently staged user, or if none exists, creates a new one.
-
Invalidation: designates a default flow to be used to invalidate a session. There are two default invalidation flows:
-
default-invalidation-flow: Used when a user logs out directly from authentik. This flow includes a User Logout stage, which ends the authentik session and triggers Single Logout for all connected applications. -
default-provider-invalidation-flow: Used when a user logs out from an application (OIDC, SAML, Proxy, or RAC providers). By default, this flow does not include a User Logout stage, meaning only the specific application session ends while the authentik session remains active. For instructions on how to also end the authentik session when a user logs out from an application, see the Single Logout documentation.
You can also create custom invalidation flows with branded background images or different logout options.
-
-
Recovery: designates a flow for recovery. This flow normally contains an Identification stage to find the user. It can also contain any amount of verification stages, such as Email or CAPTCHA. Afterwards, use the Prompt stage to ask the user for a new password and the User Write stage to update the password.
-
Stage configuration: designates a flow for general setup. This designation doesn't have any constraints in what you can do. For example, by default this designation is used to configure authenticators, like change a password and set up TOTP.
-
Unenrollment: designates a flow for unenrollment. This flow can contain any amount of verification stages, such as email or Captcha. As a final stage, to delete the account, use the user_delete stage.
Authentication: Using this option, you can configure whether the flow requires initial authentication or not, whether the user must be a superuser, if the flow can only be started after being redirected by a Redirect stage, or if the flow requires an outpost.
Behavior settings:
-
Compatibility mode: Toggle this option on to increase compatibility with password managers and mobile devices. Password managers like 1Password, for example, don't need this setting to be enabled when accessing the flow from a desktop browser. However, accessing the flow from a mobile device might necessitate this setting to be enabled.
The technical reason for this setting's existence is the JavaScript libraries we're using for the default flow interface. These interfaces are implemented using Lit, which is a modern web development library. It uses a web standard called "Shadow DOMs", which makes encapsulating styles simpler. Due to differences in Browser APIs, many password managers are not compatible with this technology.
When the compatibility mode is enabled, authentik uses a polyfill which emulates the Shadow DOM APIs without actually using the feature, and instead a traditional DOM is rendered. This increases support for password managers, especially on mobile devices.
-
Denied action: Configure what happens when access to a flow is denied by a policy. By default, authentik will redirect to a
?nextparameter if set, and otherwise show an error message.MESSAGE_CONTINUE: Show a message if no?nextparameter is set, otherwise redirect.MESSAGE: Always show error message.CONTINUE: Always redirect, either to?nextif set, otherwise to the default interface.
-
Policy engine mode: Configure the flow to succeed in any policy passes, or only if all policies pass.
Appearance Settings:
-
Layout: select how the UI displays the flow when it is executed; with stacked elements, content left or right, and sidebar left or right.
-
Background: optionally, select a background image for the UI presentation of the flow. This overrides any default background image configured in the Branding settings.
Edit or delete a flow
-
To edit a flow, navigate to Flows and Stages > Flows in the Admin interface, and then click Edit for the flow that you want to modify.
-
To delete a flow, navigate to Flows and Stages > Flows in the Admin interface, select the checkbox in front of the flow that you want to delete, and then click Delete. You can retrieve and re-apply that flow by following the steps above to create a new flow.